
Guest Post by Geary Sikich (first posted on CERM ® RISK INSIGHTS – reposted here with permission)
Introduction
There exists an overabundance of guidance for conducting risk assessments. Yet, it seems that we still have difficulty in getting risk assessments to reflect the appropriate level of concern for the identified risks that we are assessing. We also tend to view risk in relation to the place where we are employed and the industry that we work in. When we look at risk assessment from this perspective it should be clear that we are missing the point precisely, or at best, are being too narrowly focused, when it comes to assessing risk for our organizations.
This is not to say that our efforts are wasted. The risk assessment process is valuable regardless of how limited or narrowly focused it is. So, the question we should be asking ourselves as we prepare to implement a risk assessment is: “What future are we planning for?”
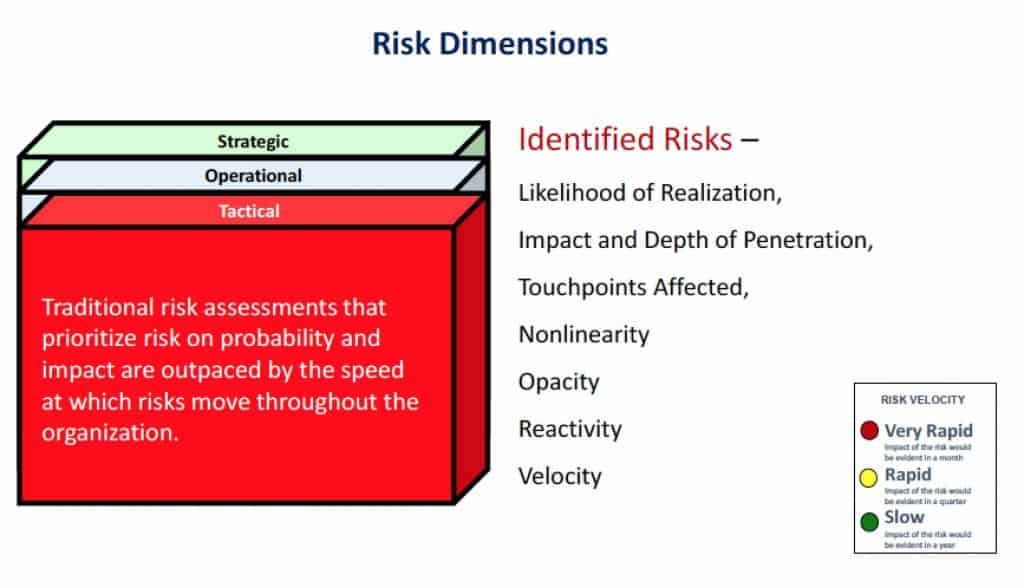
Risk Dimensions
When thinking of risk, it is perhaps helpful to structure risk into spheres and then sub-categories that take the assessment to more definitive analysis. Since risk is multi-dimensional we need to take a holistic view of our analysis process. In this respect one can simplify the dimensions by breaking risk into three categories: Strategic, Operational and Tactical. As depicted in figure 1, entitled, “Risk Dimensions”, these categories can then be further organized based on likelihood of realization, impact and depth of penetration, touchpoints affected, nonlinearity, opacity, reactivity and velocity (not necessarily all inclusive).
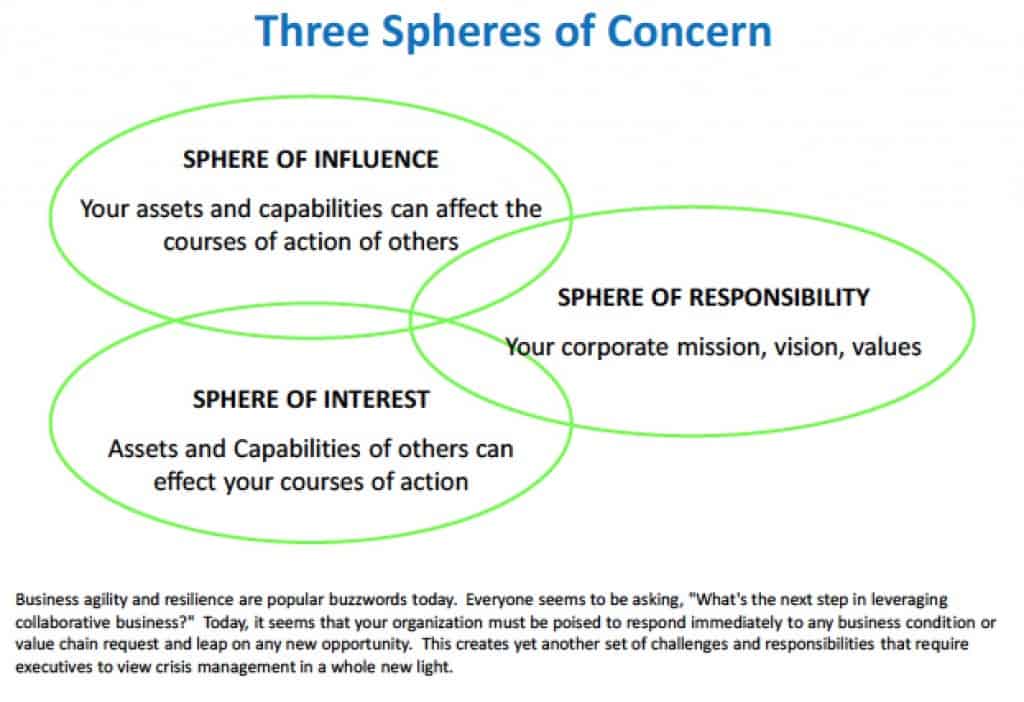
Risk Spheres
There are three spheres that reflect risk. These are depicted in Figure 2, entitled, “Three Spheres of Concern”. The first sphere (Sphere of Influence) reflects risks that your organization capabilities and assets can affect the courses of action of other organizations. The second sphere (Sphere of Interest) reflects the risks presented to your organization via the assets and capabilities that other organizations possess that influence your courses of action (reaction). The final sphere (Sphere of Responsibility) reflect the risks that you have control over and that shape your organization’s mission, vision and values. Combining the analysis from Risk Dimensions with Risk Spheres can facilitate a more comprehensive analysis of the risks that your organization faces; and, it can allow for the allocation of assets to address the risks on a continual basis, adjusting as necessary to maintain risk parity.
In this way you can create “Risk Pools” that allow your organization to focus on risks that actually present a clear and present danger to the organization, your “value chain” and other touchpoints.
Unclear but Present Dangers
Because we continue to focus our attention on readily apparent risks, we tend to overlook the risks that loom just over the horizon so to speak. For example, the Business Continuity Institute (BCI) recently published its list of the top ten global threats to business continuity. As identified by the report, this year’s global top 10 threats to business continuity are:
- Cyberattack – static
- Data breach – up 1
- Unplanned IT and telecom outages – down 1
- Act of terrorism – up 5
- Security incident – up 1
- Interruption to utility supply – down 2
- Supply chain disruption – down 2
- Adverse weather – down 1
- Availability of key skills – new entry
- Health and safety incident – new entry
While I applaud the BCI on its assessment of threats, it seems that some big risk areas are not even considered and if one studies the list; it becomes again apparent that these threats are predominately focused on information technology threats. While exceedingly critical to business and government, IT is not the “business” rather it is the support mechanism for the business. Customers, products, services, assembly lines, raw materials, finances, etc. reflect the true nature of a business. You do not purchase information from an auto dealer, you purchase a vehicle; you do not purchase information from the grocer, you purchase edible foods.
At the end of 2015, I wrote a short article on 2016 Threats, entitled, “2016 – Threat Analysis: The Year Ahead”. Below are the categories that I indicated should be on the radar screens of planners for this year. We are still plagued by the same issues, biases and lack of learning from the past:
For more detail you can find my articles readily available via the Internet. If we organize the two threat (risk) lists we can begin to categorize them into the three risk dimensions and risk spheres. From there you can actually begin to determine a risk buffering strategy that allocates assets and capabilities to the risk that allow for a parity of resources, focus and determination of likelihood of occurrence, impact, etc.
Concluding Thoughts
While Senior Executives and Board members acknowledge the need to act proactively on risks, threats, hazards, etc., their focus, generally, is in the area of Governance, Risk and Compliance (GRC) primarily at the operational and strategic levels. In order to get the resources needed to address risks of immediate concern (tactical level), your risk assessment needs to elevate its focus and tie the risks of immediate concern to the broader operational and strategic risks that management focuses on.
Begin to look at and assess the nonlinear risks that have high consequence to your organization. For example, “Sovereign Debt” presents a risk to the organization if a default occurs resulting in inflation, currency debasement and/or deflation. What happens to your budget when suddenly the currency you use becomes less valuable or becomes scarcer? Do not be placated by governmental platitudes and actions regarding the current economic situation.
Another example that is currently being overlooked is the situation within North Korea. Recently, “World Affairs” published an article by a Chinese General stating that China will have to prepare for war because of North Korea’s recent missile launch. South Korea has cut gas supplies to a joint initiative industrial park and the US and South Korea a discussing additional missile defense initiatives.
While the two examples provided above present difficult analyses regarding how to address the risks presented, they do get to the point of the need for depth in the analysis of risk. Perhaps these are low probability of occurrence risks that require little or no expenditure of assets to buffer; but the consequences are potentially devastating if they are realized.
Can you afford not to be aware, concerned and have a contingency plan under development for the three levels of risk (tactical, operational, strategic)?
Copyright© Geary W. Sikich 2016. World rights reserved. Published with permission of the author.
Bio:
Geary Sikich – Entrepreneur, consultant, author and business lecturer
Contact Information: E-mail: G.Sikich@att.net or gsikich@logicalmanagement.com. Telephone: 1- 219-922-7718.
Geary Sikich is a seasoned risk management professional who advises private and public sector executives to develop risk buffering strategies to protect their asset base. With a M.Ed. in Counseling and Guidance, Geary’s focus is human capital: what people think, who they are, what they need and how they communicate. With over 25 years in management consulting as a trusted advisor, crisis manager, senior executive and educator, Geary brings unprecedented value to clients worldwide.
Geary is well-versed in contingency planning, risk management, human resource development, “war gaming,” as well as competitive intelligence, issues analysis, global strategy and identification of transparent vulnerabilities. Geary began his career as an officer in the U.S. Army after completing his BS in Criminology. As a thought leader, Geary leverages his skills in client attraction and the tools of LinkedIn, social media and publishing to help executives in decision analysis, strategy development and risk buffering. A well-known author, his books and articles are readily available on Amazon, Barnes & Noble and the Internet
 Ask a question or send along a comment.
Please login to view and use the contact form.
Ask a question or send along a comment.
Please login to view and use the contact form.
Leave a Reply